Analysis
Overview
Analysis is a set of charts, tables, and other visualizations of data collected from the Zyxel Devices. Analysis provides a big-picture overview of network activity, while making it easy to “drill down” into granular detail on what users are doing.
Tutorial
In the Analysis section, the charts can be clicked to reveal event records.
In most cases, you can choose to analyze data collected over one of five time frames (see Dashboard):
• Last hour
• Last 24 hours
• Last 7 days
• Last 30 days
• Custom Range – click an allowed start and end day, select the time frame, and then click Apply.
This tutorial uses the following example to show how to explore an URL threat filter hit detail that you want to investigate, specifically by destination IP.
1 Click Analysis > Security Indicator > URL Threat Filter.
Analysis > Security Indicator > URL Threat Filter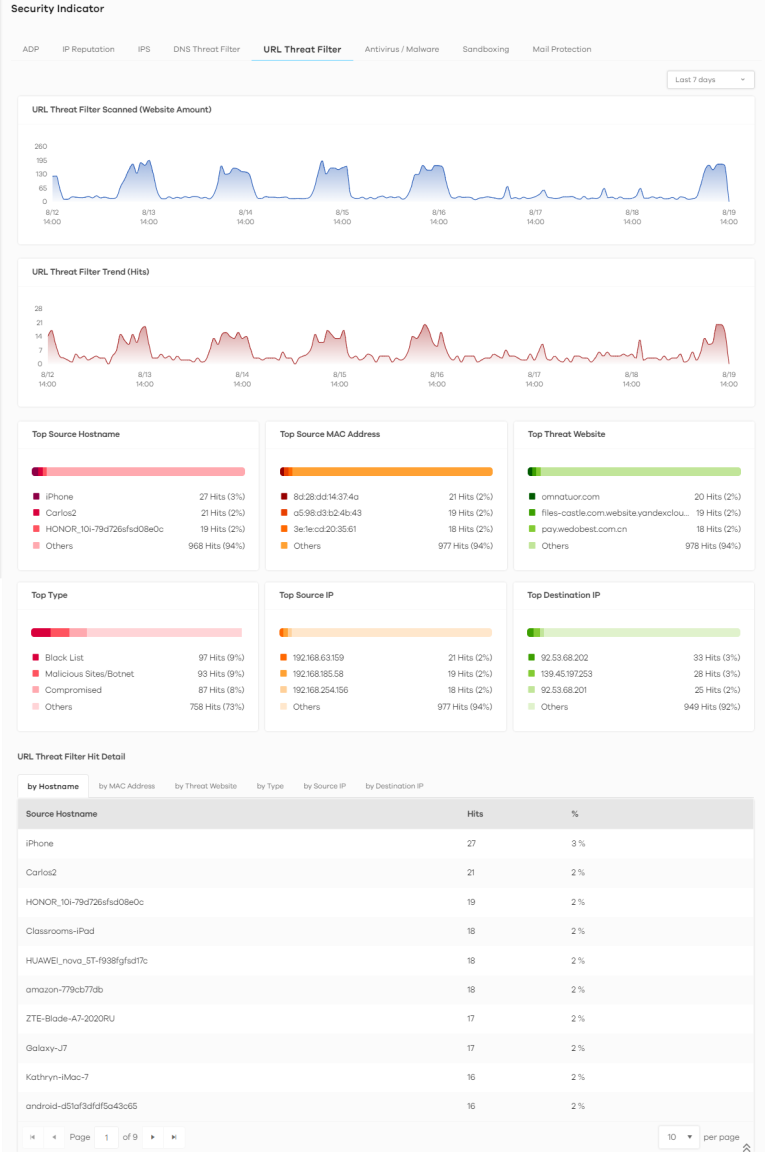

2 Click the by Destination IP tab. To display the next set of malware or viruses, click the arrow on the lower left of the screen.
Analysis > Security Indicator > URL Threat Filter > by Destination IP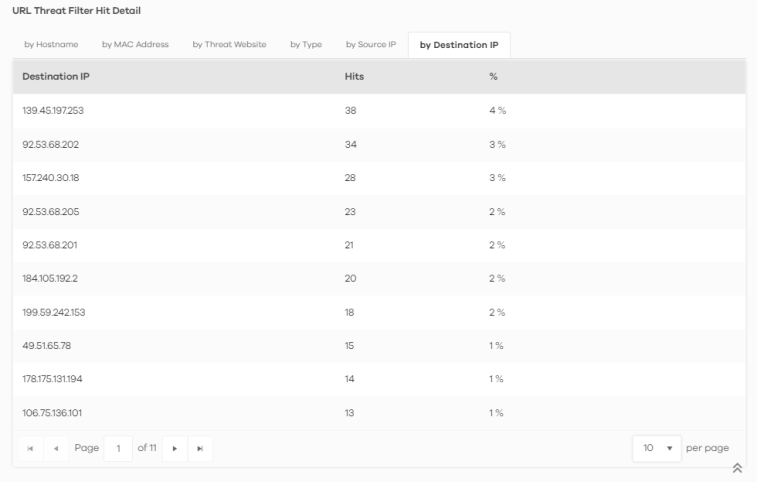

3 Clicking a Destination IP will display its Threat Website address, the number of Hits, and the percentage (%) of hits to the destination IP address.
Analysis > Security Indicator > URL Threat Filter > by Source IP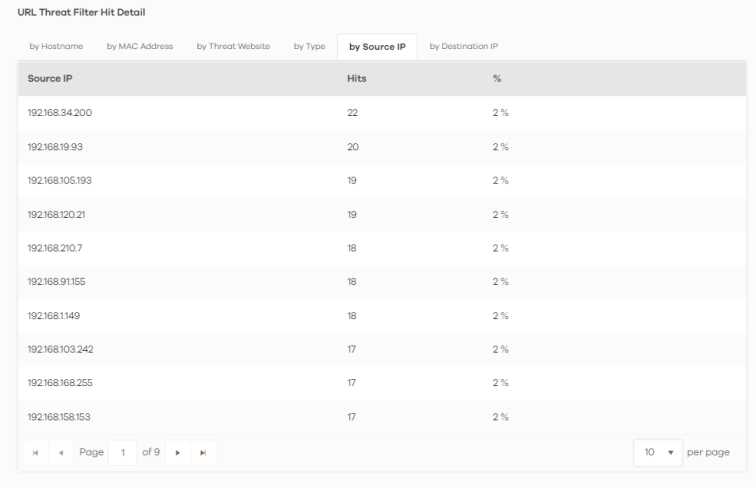

4 Clicking a Source IP will display its Threat Website address, the number of Hits, and the percentage (%) of hits from the source IP address.
Source IP Information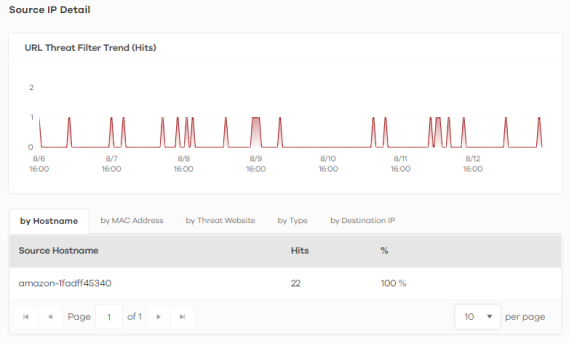

Sandboxing
Zyxel cloud sandboxing is a security mechanism which provides a safe environment to separate running programs from your network and host devices. Unknown or untrusted programs or codes are uploaded to a cloud server and executed within an isolated virtual machine (VM) to monitor and analyze the zero-day malware and advanced persistent threats (APTs) that may evade the Zyxel Device’s detection, such as anti-malware. Results of cloud sandboxing are sent from the server to the Zyxel Device.
The Zyxel Device sandboxing checks all received files against its local cache for known malicious or suspicious codes. Files with no detected malicious or suspicious codes found in the cache (‘unknown’) are copied and uploaded to the security cloud server (S) for further inspection. The scan result from the cloud server is added to the Zyxel Device cache and used for future inspection.
General Zyxel Sandboxing Inspection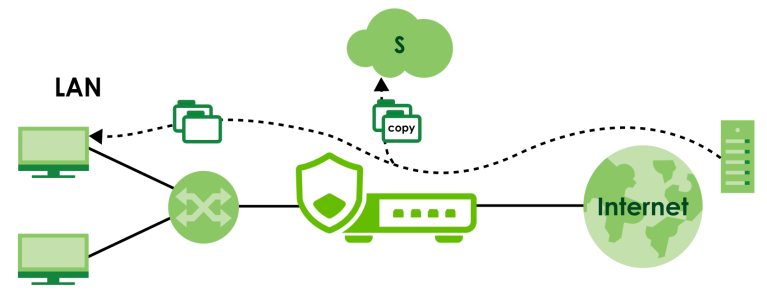

In the Zyxel Device, you can configure Advanced Zyxel Sandboxing Inspection to hold and inspect unknown downloaded files for up to 2 seconds. After 2 seconds the Zyxel Device forwards the file even if the inspection is incomplete.
Advanced Zyxel Sandboxing Inspection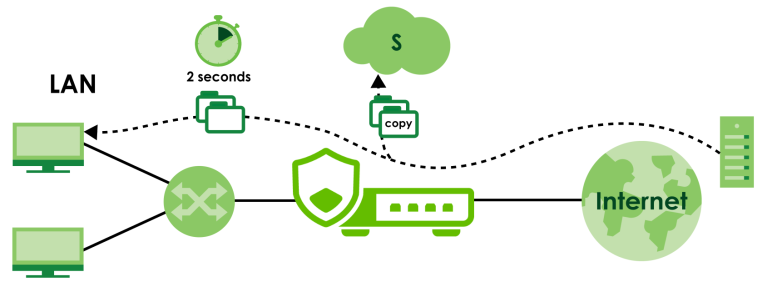

Supported File Types for Sandboxing Inspection
Sandboxing can only check the types of files listed under File Submission Options in the Sandboxing screen of the Zyxel Device. If you disabled Scan and detect EICAR test virus in the Anti Malware screen, then EICAR test files will be sent to Sandboxing.
The EICAR test file is a standardized test file for signature based anti-malware scanners. When the scanner detects the EICAR file, it responds in the same way as if it found a real malware. Besides straightforward detection, the EICAR file can also be compressed to test whether the anti-malware software can detect it in a compressed file.
Turning on Sandboxing on Your Zyxel Device
To use the sandboxing function, you need to register your Zyxel Device and activate the service license at myZyxel, and then turn on the sandboxing function on the Zyxel Device.
Sandboxing Alerts
SecuReporter sends sandboxing alerts to Zyxel Device administrators when:
1 The Zyxel Device forwarded files that were later discovered to be suspicious or malicious.
2 The Zyxel Device sandboxing (or Security Cloud) removed infected portions of files that were suspicious or malicious.