Network Activity Logs
Network activity logs are categorized as follows:
The following figure shows the Search > Log > Network Activity screen.
Search > Log > Network Activity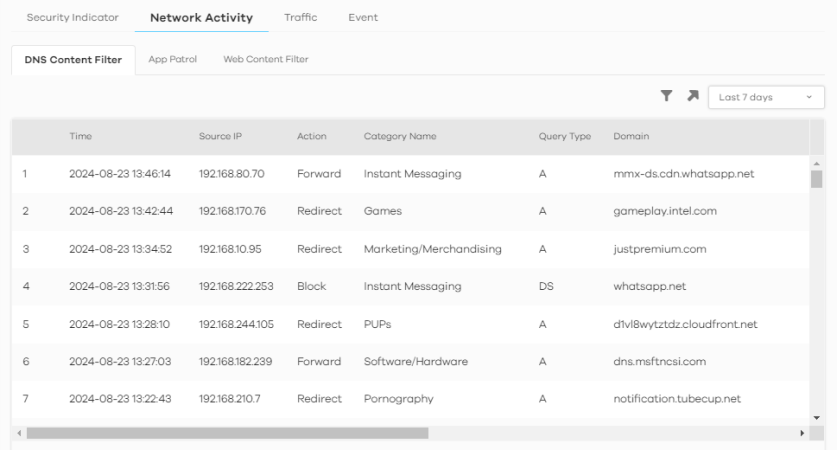

The following table describes the labels on the Search > Log > Network Activity screen.
Label | DESCRIPTION |
|---|---|
 | Click Clear All to discard the filtering rules. Click Add Rule to create and manage the detailed filtering rules for each label. Click Search to apply the filtering rule to the log search. Click --Please Select-- to set the filtering rule for each label. Click  to discard a filtering rule. to discard a filtering rule.The  will appear for the following reasons. Hover the mouse cursor on it to know the type of error. will appear for the following reasons. Hover the mouse cursor on it to know the type of error.• Please select a field. This occurs when you click the Search button without selecting a field. • Please enter a value before clicking ‘Search’. This occurs when you click the Search button without entering or selecting a value in the contains field. • Press ‘Enter’ to apply. This occurs when you click the Search button without pressing the Enter key for the contains field that can accept multiple values. • The value cannot be found. This occurs when you enter a none existent value in the contains field. • No log available. This occurs when no log is available for the filter value you enter or select. • The value cannot be found. This occurs when entering the wrong character format in the contains field (for example, entering alphabetic characters for the Source IP field). |
 | Click  to have SecuReporter save the result of your log search to your computer in a CSV file. Maximum of 10,000 search results. Fields that do not have a value in the log search result will appear as blanks in the CSV file. to have SecuReporter save the result of your log search to your computer in a CSV file. Maximum of 10,000 search results. Fields that do not have a value in the log search result will appear as blanks in the CSV file. |
Depending on your license type, select the time frame by clicking a ‘from’ and ‘to’ dates. You can also specify the ‘from’ and ‘to’ hh:mm time range (24-hour format). Then click Apply to display those logs. | |
Time | Select the year-month-date hour:minute:second of the log. When adding this as a filter rule, click the drop-down field on the right of the screen to select the time frame. |
Source IP | Enter the IPv4 or IPv6 address of the original sender of the packet. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 192.168.221.* (It will search for logs with any IP within 192.168.221.0 – 192.168.221.255). |
Source Port | Enter the port number of the original sender of the packet. When adding this as a filter rule, enter the port number and press Enter. More than one port number can be entered after the first filter rule by entering another port number and pressing Enter. Multiple port number filters are entered one at a time. |
Destination IP | Enter the IPv4 or IPv6 address of the final destination of the packet. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 210.61.209.* (It will search for logs with any IP within 210.61.209.0 – 210.61.209.255). |
Destination Port | Enter the port number of the final destination of the packet. When adding this as a filter rule, enter the port number and press Enter. More than one port number can be entered after the first filter rule by entering another port number and pressing Enter. Multiple port number filters are entered one at a time. |
Action (DNS Content Filter) | Enter how the Zyxel Device handle threats posed by domains (Block, Redirect, Forward). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
Action (App Patrol) | Enter how the Zyxel Device handle threats posed by applications (reject, drop, forward). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
Action (Web Content Filter) | Enter how the Zyxel Device handle threats posed by websites (forward, block, warning). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
User | Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the user name is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, USER-698a9b31-cea4-523c-8955-ffad47db967e. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |
Application Category Name | Enter the most common types of applications as detected by the Zyxel Device. Application categories include Application Service, Instant Messaging, Web, Encrypted, and so on. When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one application category can be entered after the first filter rule by entering another application category and pressing Enter. Multiple application category filters are entered one at a time. |
Application Name | Enter the most frequently visited applications (a wildcard is allowed) as detected by the Zyxel Application Patrol. App Patrol manages general protocols (for example, HTTP and FTP), instant messenger (IM), peer-to-peer (P2P), Voice over IP (VoIP), streaming (RSTP) applications and even an application’s individual features (like text messaging, voice, video conferencing, and file transfers). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one application name can be entered after the first filter rule by entering another application name and pressing Enter. Multiple application name filters are entered one at a time. |
Web Category Name | Enter the most common types of threats posed by websites blocked by the Zyxel Device as detected by the URL Threat Filter. Threat categories include Unrated, Anonymizers, Compromised, Phishing and Fraud, Spam Sites, Malware, Botnets, and so on. When adding this as a filter rule, enter the web category name or part of the web category name you want to find to enable SecuReporter auto suggestion. More than one web category name can be entered after the first filter rule by entering another web category name and pressing Enter. Multiple web category name filters can be entered one at a time. |
Website | Enter the website (a wildcard is allowed) to screen the most common threats by websites blocked by the Zyxel Device. When adding this as a filter rule, enter the website or part of the website you want to find to enable SecuReporter auto suggestion. |
Query Type | Enter the DNS record types for accessed domains that were blocked. DNS record types include A, AAAA, HTTPS, TXT and so on. When adding this as a filter rule, select from the drop-down list. More than one query type can be entered after the first filter rule by entering another query type and pressing Enter. Multiple query type filters are entered one at a time. |
Domain | Enter the URL of FQDNs that may pose a security threat to network devices behind the Zyxel Device. When adding this as a filter rule, select from the drop-down list. More than one domain can be entered after the first filter rule by entering another domain and pressing Enter. Multiple domain filters are entered one at a time. |
Rule | Enter the name of the policy control rule the the connection is using. When adding this as a filter rule, select from the drop-down list. More than one rule can be entered after the first filter rule by entering another domain and pressing Enter. Multiple domain filters are entered one at a time. |
Source Hostname | This is the hostname of the original sender of the packet. |
Source MAC Address | This is the MAC address of the original sender of the packet. |
Device Category | This is the device type of the original sender of the packet. |
Device OS | This is the device operating system of the original sender of the packet. |
Traffic Logs
The following figure shows the Search > Log > Traffic screen.
Search > Log > Traffic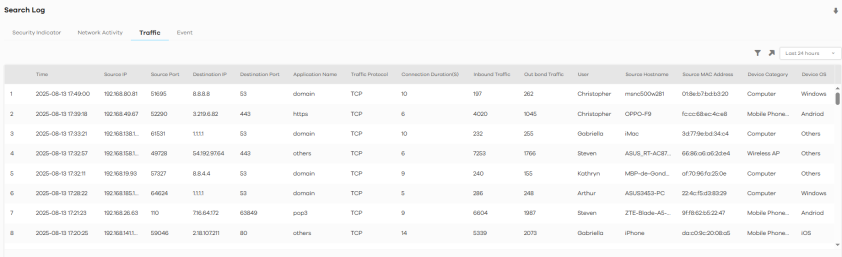

The following table describes the labels on the Search > Log > Traffic screen.
Label | DESCRIPTION |
|---|---|
 | Click Clear All to discard the filtering rules. Click Add Rule to create and manage the detailed filtering rules for each label. Click Search to apply the filtering rule to the log search. Click --Please Select-- to set the filtering rule for each label. Click  to discard a filtering rule. to discard a filtering rule.The  will appear for the following reasons. Hover the mouse cursor on it to know the type of error. will appear for the following reasons. Hover the mouse cursor on it to know the type of error.• Please select a field. This occurs when you click the Search button without selecting a field. • Please enter a value before clicking ‘Search’. This occurs when you click the Search button without entering or selecting a value in the contains field. • Press ‘Enter’ to apply. This occurs when you click the Search button without pressing the Enter key for the contains field that can accept multiple values. • The value cannot be found. This occurs when you enter a none existent value in the contains field. • No log available. This occurs when no log is available for the filter value you enter or select. • The value cannot be found. This occurs when entering the wrong character format in the contains field (for example, entering alphabetic characters for the Source IP field). |
 | Click  to have SecuReporter save the result of your log search to your computer in a CSV file. Maximum of 10,000 search results. Fields that do not have a value in the log search result will appear as blanks in the CSV file. to have SecuReporter save the result of your log search to your computer in a CSV file. Maximum of 10,000 search results. Fields that do not have a value in the log search result will appear as blanks in the CSV file. |
Depending on your license type, select the time frame by clicking a ‘from’ and ‘to’ dates. You can also specify the ‘from’ and ‘to’ hh:mm time range (24-hour format). Then click Apply to display those logs. | |
Time | Select the year-month-date hour:minute:second of the log. When adding this as a filter rule, click the drop-down field on the right of the screen to select the time frame. |
Source IP | Enter the IPv4 or IPv6 address of the original sender of the packet. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 192.168.221.* (It will search for logs with any IP within 192.168.221.0 – 192.168.221.255). |
Source Port | Enter the port number of the original sender of the packet. When adding this as a filter rule, enter the port number and press Enter. More than one port number can be entered after the first filter rule by entering another port number and pressing Enter. Multiple port number filters are entered one at a time. |
Destination IP | Enter the IPv4 or IPv6 address of the final destination of the packet. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 210.61.209.* (It will search for logs with any IP within 210.61.209.0 – 210.61.209.255). |
Destination Port | Enter the port number of the final destination of the packet. When adding this as a filter rule, enter the port number and press Enter. More than one port number can be entered after the first filter rule by entering another port number and pressing Enter. Multiple port number filters are entered one at a time. |
Application Name | Enter the most frequently visited applications (case sensitive) as detected by the Zyxel Application Patrol. APP Patrol manages general protocols (for example, HTTP and FTP), instant messenger (IM), peer-to-peer (P2P), Voice over IP (VoIP), streaming (RSTP) applications and even an application’s individual features (like text messaging, voice, video conferencing, and file transfers). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one application can be entered after the first filter rule by entering another application and pressing Enter. Multiple application filters are entered one at a time. |
Traffic Protocol | Enter the type of transport packet being carried (TCP/UDP/OTHERS). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one traffic protocol can be entered after the first filter rule by entering another traffic protocol and pressing Enter. Multiple traffic protocol filters are entered one at a time. |
Connection Duration(S) | This is the length of the network session in seconds. |
Inbound Traffic | This is the amount of information received by the source in the network session. |
Outbound Traffic | This is the amount of information transmitted by the source in the network session. |
User | Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the user name is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, USER-698a9b31-cea4-523c-8955-ffad47db967e. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |
Astra Email | This is the Astra user’s mail address of the original sender of the packet. You see this only if devices on your network are using Astra, which is an email identification service that helps trace suspicious traffic back to the specific user account. |
Source Hostname | This is the hostname of the original sender of the packet. |
Source MAC Address | This is the MAC address of the original sender of the packet. |
Device Category | This is the device type of the original sender of the packet. |
Device OS | This is the device operating system of the original sender of the packet. |
Event Logs
Event logs are categorized as follows:
• User Login
• Device Event
• DHCP
The following figure shows the Search > Log > Event screen.
Search > Log > Event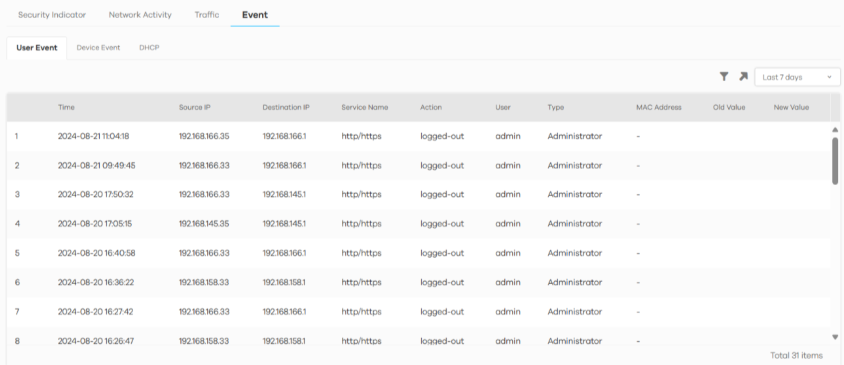

The following table describes the labels on the Search > Log > Event screen.
Label | DESCRIPTION |
|---|---|
 | Click Clear All to discard the filtering rules. Click Add Rule to create and manage the detailed filtering rules for each label. Click Search to apply the filtering rule to the log search. Click --Please Select-- to set the filtering rule for each label. Click  to discard a filtering rule. to discard a filtering rule.The  will appear for the following reasons. Hover the mouse cursor on it to know the type of error. will appear for the following reasons. Hover the mouse cursor on it to know the type of error.• Please select a field. This occurs when you click the Search button without selecting a field. • Please enter a value before clicking ‘Search’. This occurs when you click the Search button without entering or selecting a value in the contains field. • Press ‘Enter’ to apply. This occurs when you click the Search button without pressing the Enter key for the contains field that can accept multiple values. • The value cannot be found. This occurs when you enter a none existent value in the contains field. • No log available. This occurs when no log is available for the filter value you enter or select. • The value cannot be found. This occurs when entering the wrong character format in the contains field (for example, entering alphabetic characters for the Source IP field). |
 | Click  to have SecuReporter save the result of your log search to your computer in a CSV file. Maximum of 10,000 search results. Fields that do not have a value in the log search result will appear as blanks in the CSV file. to have SecuReporter save the result of your log search to your computer in a CSV file. Maximum of 10,000 search results. Fields that do not have a value in the log search result will appear as blanks in the CSV file. |
Depending on your license type, select the time frame by clicking a ‘from’ and ‘to’ dates. You can also specify the ‘from’ and ‘to’ hh:mm time range (24-hour format). Then click Apply to display those logs. | |
Time | Select the year-month-date hour:minute:second of the log. When adding this as a filter rule, click the drop-down field on the right of the screen to select the time frame. |
Source IP | Enter the IPv4 or IPv6 address of the original sender of the packet. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 192.168.221.* (It will search for logs with any IP within 192.168.221.0 – 192.168.221.255). |
Destination IP | Enter the IPv4 or IPv6 address of the final destination of the packet. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 210.61.209.* (It will search for logs with any IP within 210.61.209.0 – 210.61.209.255). |
Service Name | Enter the login method (console, http/https, ssh). When adding this as a filter rule, enter the service name or part of the service name you want to find to enable SecuReporter auto suggestion. More than one service name can be entered after the first filter rule by entering another service name and pressing Enter. Multiple service name filters can be entered one at a time. |
Action Event > User Login | Enter the status of the login attempt (Failed-login / logged-in / logged-out). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
Action Event > DHCP | Enter the action of assigning an IP address to a device by the DNS server or release (assigned and release). When adding this as a filter rule, enter the action or part of the action you want to find to enable SecuReporter auto suggestion. Both assigned and release can be entered as a filter rule by entering assigned and pressing Enter, and then entering release and pressing Enter. |
Assign IP | This is the IPv4 or IPv6 address currently assigned to a DHCP client or reserved for a specific MAC address. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 192.168.221.* (It will search for logs with any IP within 192.168.221.0 – 192.168.221.255). |
User | Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the user name is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, USER-698a9b31-cea4-523c-8955-ffad47db967e. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |
Type | Enter the role type (a wildcard is allowed) of the event’s login attempt (Administrator, Limited-Admin, User). When adding this as a filter rule, enter the role type or part of the role type you want to find to enable SecuReporter auto suggestion. |
MAC Address Event > User Login | Enter the Zyxel Device’s MAC address (case sensitive) during the event’s login attempt. Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the MAC address is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, MAC-5ba49d8a-d027-5c76-bf28-a45857f780bc. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |
MAC Address Event > DHCP | Enter the MAC address (case sensitive) to which the IP address is currently assigned or for which the IP address is reserved. Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the MAC address is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, MAC-5ba49d8a-d027-5c76-bf28-a45857f780bc. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |
Device Event | This displays boot-up as the Zyxel Device event. |
Host Name | Enter the unique name (case sensitive) by which a device is known on a network. The Zyxel Device learns these from the DHCP client requests. Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the host name is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, HOST-8c9f2269-c7fa-55e5-b36f-d8987efd11ee. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |