Search Log
Search log allows you to display Zyxel Device logs based on a time frame and also export them in CSV format for further analysis. You must enable logs to be sent to SecuReporter in the Web Configurator of the Zyxel Device or NCC. You can select Security Indicator, Network Activity, Traffic and Event logs to view. The field on the right of  allow you to select a specific time frame to view. The default is the last 7 days. You can change the time frame depending on your license type, see Search > Log > Network Activity Screen for details.
allow you to select a specific time frame to view. The default is the last 7 days. You can change the time frame depending on your license type, see Search > Log > Network Activity Screen for details.
 allow you to select a specific time frame to view. The default is the last 7 days. You can change the time frame depending on your license type, see Search > Log > Network Activity Screen for details.
allow you to select a specific time frame to view. The default is the last 7 days. You can change the time frame depending on your license type, see Search > Log > Network Activity Screen for details.Search Log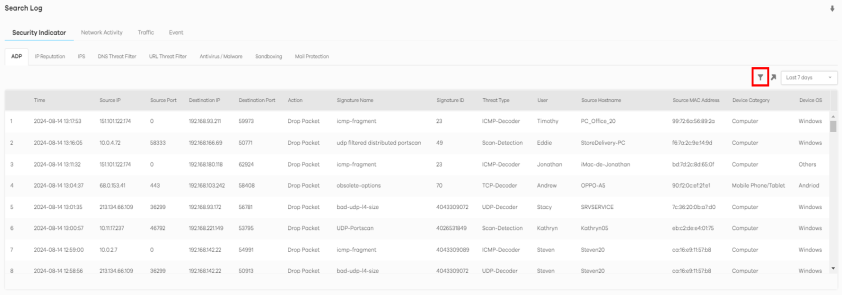

You can set the search log criteria by clicking  , see Search > Log > Network Activity Screen for details.
, see Search > Log > Network Activity Screen for details.
 , see Search > Log > Network Activity Screen for details.
, see Search > Log > Network Activity Screen for details.The screen displays 100 search results at a time. Scroll down to load the next 100.
Log Search Privileges
This table summarizes the SecuReporter log search privileges:
type | SecuReporter |
|---|---|
Security Logs Date Range | Past 30 days |
Traffic Logs Date Range | Past 7 days |
Custom Range | Yes |
Filters | Yes |
CSV file download | Yes |
Download Logs
You can download the Zyxel Device’s logs by doing the following steps.
1 Go to the Log screen. Click the Download History Data icon  at the upper-right corner.
at the upper-right corner.
 at the upper-right corner.
at the upper-right corner.2 Select the log files you want and click Request to Download, or click Request to Download All to download all log files from up to 1 year at once.
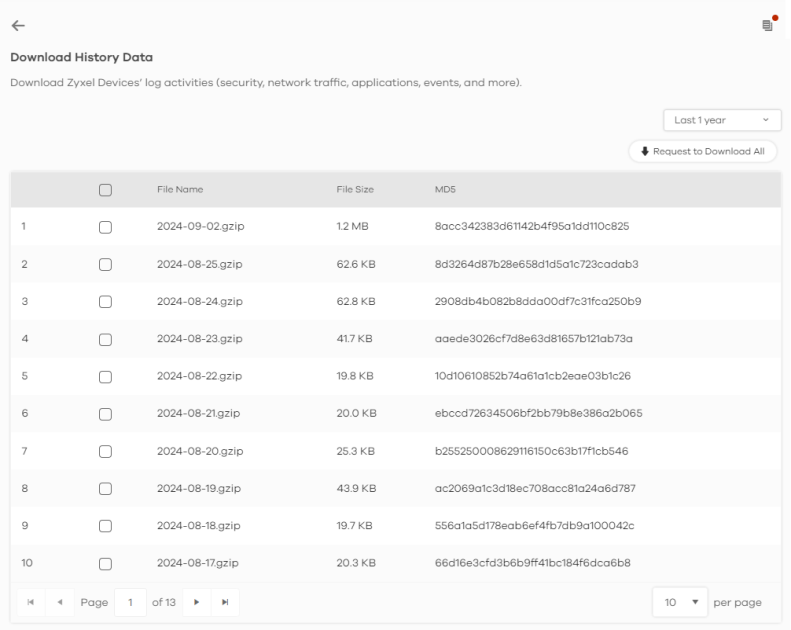
3 The following window pops up. Click Done to proceed.
4 Click the History Data icon at the upper-right corner.
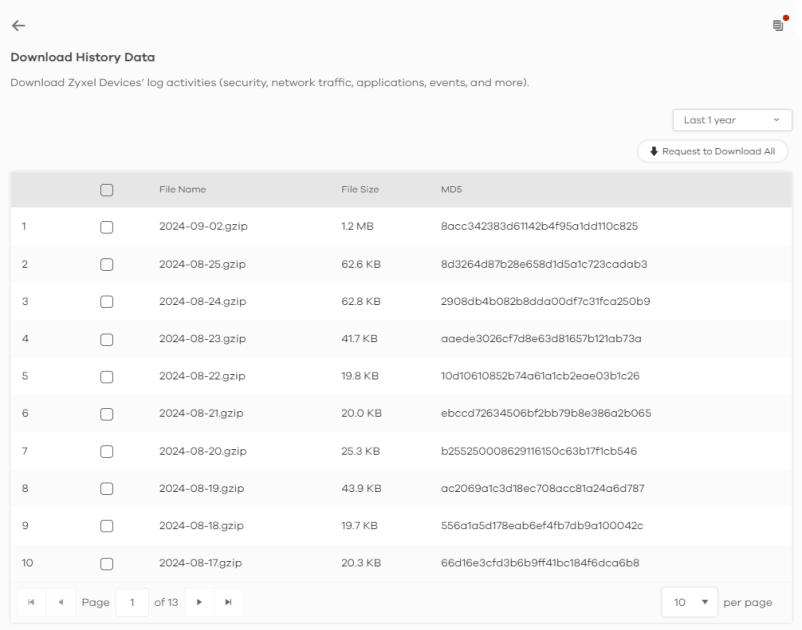
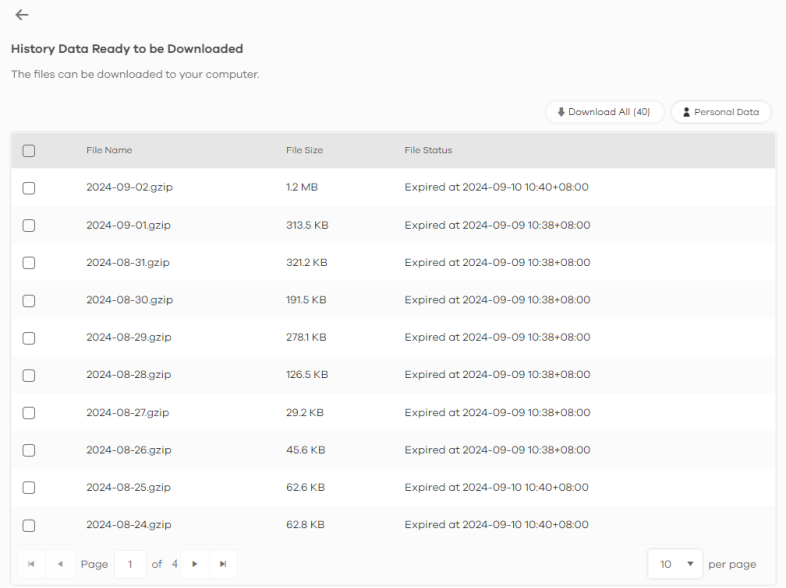
5 The log files ready for download will be displayed on this screen. Select the log files you want and click Download to download them in ZIP format, or click Download All to download all logs from up to 1 year in ZIP format to your computer.
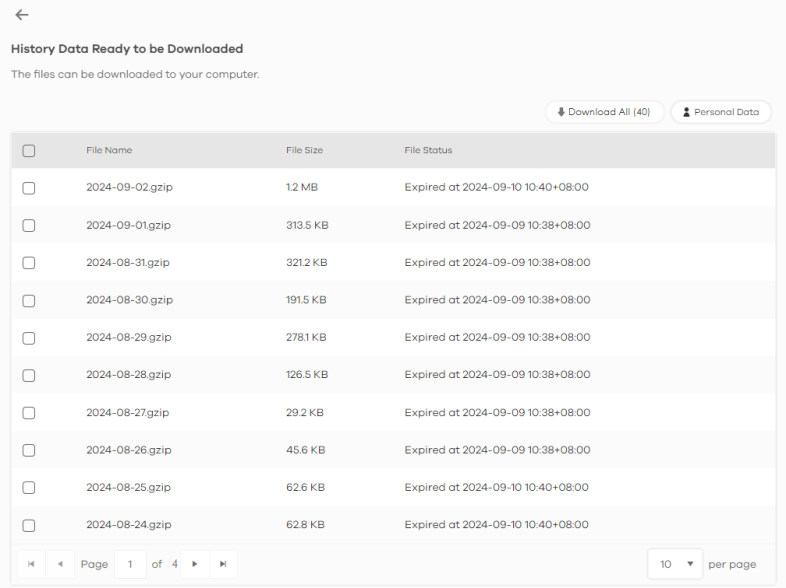
6 If you select Fully Anonymous as the Protection Policy, the hostname in the log files will be encrypted. You will need to download Personal Data to refer to the hostname.
Security Indicator Logs
Security Indicator logs are categorized as follows:
• ADP
• IPS
The following figure shows the Search > Log > Security Indicator screen.
Search > Log > Security Indicator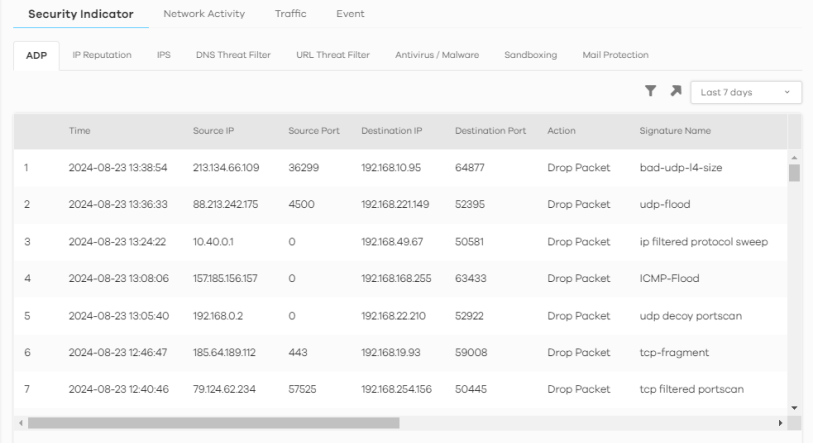

The following table describes the labels on the Search > Log > Security Indicator screen.
Label | DESCRIPTION |
|---|---|
 | Click Clear All to discard the filtering rules. Click Add Rule to create and manage the detailed filtering rules for each label. Click Search to apply the filtering rule to the search log. Click --Please Select-- to set the filtering rule for each label. Click  to discard a filtering rule. to discard a filtering rule.The  will appear for the following reasons. Hover the mouse cursor on it to know the type of error. will appear for the following reasons. Hover the mouse cursor on it to know the type of error.• Please select a field. This occurs when you click the Search button without selecting a field. • Please enter a value before clicking ‘Search’. This occurs when you click the Search button without entering or selecting a value in the contains field. • Press ‘Enter’ to apply. This occurs when you click the Search button without pressing the Enter key for the contains field that can accept multiple values. • The value cannot be found. This occurs when you enter a none existent value in the contains field. • No log available. This occurs when no log is available for the filter value you enter or select. • The value cannot be found. This occurs when entering the wrong character format in the contains field (for example, entering alphabetic characters for the Source IP field). |
 | Click  to have SecuReporter save the result of your search log to your computer in a CSV file. Maximum of 10,000 search results. Fields that do not have a value in the search log result will appear as blanks in the CSV file. to have SecuReporter save the result of your search log to your computer in a CSV file. Maximum of 10,000 search results. Fields that do not have a value in the search log result will appear as blanks in the CSV file. |
Depending on your license type, select the time frame by clicking a ‘from’ and ‘to’ dates. You can also specify the ‘from’ and ‘to’ hh:mm time range (24-hour format). Then click Apply to display those logs. | |
Time | Select the year-month-date hour:minute:second of the log. When adding this as a filter rule, click the drop-down field on the right of the screen to select the time frame. |
Source IP | Enter the IPv4 or IPv6 address of the original sender of the packet. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 192.168.221.* (It will search for logs with any IP within 192.168.221.0 - 192.168.221.255). |
Source Port | Enter the port number of the original sender of the packet. When adding this as a filter rule, enter the port number and press Enter. More than one port number can be entered after the first filter rule by entering another port number and pressing Enter. Multiple port number filters are entered one at a time. |
Destination IP | Enter the IPv4 or IPv6 address of the final destination of the packet. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 210.61.209.* (It will search for logs with any IP within 210.61.209.0 - 210.61.209.255). |
Destination Port | Enter the port number of the final destination of the packet. When adding this as a filter rule, enter the port number and press Enter. More than one port number can be entered after the first filter rule by entering another port number and pressing Enter. Multiple port number filters are entered one at a time. |
Action (IPS/ADP) | Enter the response the Zyxel Device takes when a packet matches a signature. A signature is a pattern of malicious or suspicious packet activity. This is defined in the profile screen of your Zyxel Device’s Web Configurator. The Zyxel Device checks all signatures and continues searching even after a match is found. If two or more rules have conflicting actions for the same packet, then the Zyxel Device applies the more restrictive action (Reject Both, Reject Receiver or Reject Sender, Drop Packet, No Action in this order). If a packet matches a rule for Reject Receiver and it also matches a rule for Reject Sender, then the Zyxel Device will Reject Both. When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
Action (IP Reputation) | IP Reputation checks the reputation of an IP address from a database. An IP address with bad reputation associates with suspicious activities, such as spam, virus, and/or phishing. Enter how the Zyxel Device will respond when there are packets coming from an IPv4 address with bad reputation (ACCESS BLOCK and ACCESS FORWARD). When adding this as a filter rule, enter the action or part of the action you want to find to enable SecuReporter auto suggestion. Both ACCESS BLOCK and ACCESS FORWARD can be entered as a filter rule by entering ACCESS BLOCK and pressing Enter, and then entering ACCESS FORWARD and pressing Enter. |
Action (DNS Filter) | Enter how the Zyxel Device handle threats posed by FQDNs (Block, Redirect). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
Action (URL Threat Filter) | Enter how the Zyxel Device handle threats posed by URLs (Uniform Resource Locators) (ACCESS BLOCK, ACCESS WARNING, ACCESS PASS). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
Action (Antivirus / Malware) | Enter ACCESS FORWARD when a service can be used to access the Zyxel Device. Otherwise, it is ACCESS BLOCK. Enter FILE FORWARD when a file is allowed. Otherwise, it is FILE DESTROY. When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
Action (Sandboxing) | The Zyxel Device sandboxing checks all received files against its local cache for known malicious or suspicious codes. Enter how the Zyxel Device handle sandboxing (Pass, Detected, Destroy). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one action can be entered after the first filter rule by entering another action and pressing Enter. Multiple action filters are entered one at a time. |
Action (Mail Protection) | Enter how the Zyxel Device handle spam SMTP/POP3 email (MAIL FORWARD, MAIL DROP). When adding this as a filter rule, enter the action or part of the action you want to find to enable SecuReporter auto suggestion. Both MAIL FORWARD and MAIL DROP can be entered as a filter rule by entering MAIL FORWARD and pressing Enter, and then entering MAIL DROP and pressing Enter. |
User | Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the user name is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, USER-698a9b31-cea4-523c-8955-ffad47db967e. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |
Signature Name | Enter the name (case sensitive, a wildcard is allowed) of a signature. When adding this as a filter rule, enter the name or part of the name of the signature you want to find to enable SecuReporter auto suggestion. |
Signature ID | Enter the identification number of the signature. When adding this as a filter rule, enter the ID or part of the ID of the signature you want to find to enable SecuReporter auto suggestion. |
Threat Type | Enter the signature (case sensitive) by threat type. When adding this as a filter rule, enter the threat type or part of the threat type you want to find to enable SecuReporter auto suggestion. More than one threat type can be entered after the first filter rule by entering another threat type and pressing Enter. Multiple threat type filters are entered one at a time. |
Mail From | Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the sender is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, MAIL-108cef2d-b591-5460-af79-71994d126cc7. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |
Mail To | Depending on the data protection policy (see Add a Zyxel Device to an Organization for details), the following will be displayed: • For Partially Anonymous users, the recipient is displayed but log search is disabled. • For Fully Anonymous users, copy a Hash value to search for logs. For example, MAIL-108cef2d-b591-5460-af79-71994d126cc7. • For Non-Anonymous users, enter plain text (unlimited number of characters, case sensitive) for log search. |
Mail Subject | This is the title header of the incoming email. |
Protocol (Sandboxing) | Enter the method email is sent or received through the Zyxel Device (SMTP, POP3, HTTP, FTP, and Unknown). When adding this as a filter rule, enter the protocol or part of the protocol you want to find to enable SecuReporter auto suggestion. More than one protocol can be entered after the first filter rule by entering another protocol and pressing Enter. Multiple protocol filters are entered one at a time. |
Protocol (Mail Protection) | Enter the method email is sent or received through the Zyxel Device (SMTP and POP3). When adding this as a filter rule, enter the protocol or part of the protocol you want to find to enable SecuReporter auto suggestion. Both SMTP and POP3 can be entered as a filter rule by entering SMTP and pressing Enter, and then entering POP3 and pressing Enter. |
URL | Enter the URL (a wildcard is allowed) where the threat was detected. When adding this as a filter rule, enter the URL or part of the URL you want to find to enable SecuReporter auto suggestion. |
File Type | Enter the type of file sent for sandboxing inspection (Archives (.zip), Executables, MS Office Documents, Macromedia Flash Data/PDF/RTF). When adding this as a filter rule, enter the file type or part of the file type you want to find to enable SecuReporter auto suggestion. More than one file type can be entered after the first filter rule by entering another file type and pressing Enter. Multiple file type filters can be entered one at a time. |
Score Level | Enter the score given by the Defend Center for malware characteristics that has been detected through the sandboxing function (Malicious, Suspicious, and Clean). When adding this as a filter rule, enter the score level or part of the score level you want to find to enable SecuReporter auto suggestion. More than one score level can be entered after the first filter rule by entering another score level and pressing Enter. Multiple score level filters can be entered one at a time. |
Hash | Copy the hash value (a wildcard is allowed) of the file that was sent for sandboxing inspection. When adding this as a filter rule, copy the hash value or part of the hash value you want to find to enable SecuReporter auto suggestion. |
Rule Number | Enter the log search rule number. This is assigned by the Zyxel Device. When adding this as a filter rule, enter the rule number and press Enter. More than one rule number can be entered after the first filter rule by entering another rule number and pressing Enter. Multiple rule number filters are entered one at a time. |
Scan Result | Enter the scan result (White-List, Black-List, IP-Reputation, DNSBL, DNSBL-timeout, Spam, Virus, Spam-Virus, Timeout, Clear, and Phishing). When adding this as a filter rule, enter the scan result or part of the scan result you want to find to enable SecuReporter auto suggestion. More than one scan result can be entered after the first filter rule by entering another scan result and pressing Enter. Multiple scan result filters are entered one at a time. |
Severity | Enter the severity levels as defined in the Zyxel Device. (1) Very-Low, (2) Low, (3) Medium, (4) High, and (5) Severe. The number in brackets is the number you use when adding this as a filter rule. More than one severity level can be entered after the first filter rule by entering another severity level and pressing Enter. Multiple severity level filters are entered one at a time. |
Category Name | Enter the most common types of URL threats (case sensitive) as detected by the Zyxel Device. Threat categories include Malware, Spam Sites, and so on. When adding this as a filter rule, enter the category name or part of the category name you want to find to enable SecuReporter auto suggestion. More than one category name can be entered after the first filter rule by entering another category name and pressing Enter. Multiple category name filters can be entered one at a time. |
Threat Name | Enter the name of the threat (a wildcard is allowed) as detected by the Zyxel Device. The value depends on the Zyxel Device. When adding this as a filter rule, enter the threat name you want to find. |
Risk | Enter the threshold threat level to which the Zyxel Device will take action. (High, Medium, and Low). The threat level is determined by the IP reputation engine. It grades IPv4 addresses. When adding this as a filter rule, enter the threshold threat level or part of the threshold threat level you want to find to enable SecuReporter auto suggestion. More than one threshold threat level can be entered after the first filter rule by entering another threshold threat level and pressing Enter. Multiple threshold threat level filters can be entered one at a time. |
Threat Category | Enter the most common type of threats posed by IPs blocked by the Zyxel Device as detected by IP Reputation. Threat categories include Exploits, Spam Sources, Phishing, and BotNets. When adding this as a filter rule, enter the threat category or part of the threat category you want to find to enable SecuReporter auto suggestion. More than one threat category can be entered after the first filter rule by entering another threat category and pressing Enter. Multiple threat category filters can be entered one at a time. |
Risk IP | Enter the IPv4 or IPv6 address where the threat was detected. When adding this as a filter rule, enter the complete IP address or enter a wildcard such as 210.61.209.* (It will search for logs with any IP within 210.61.209.0 – 210.61.209.255). |
Virus Name | Enter the name (case sensitive, a wildcard is allowed) of a virus. When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. |
File Name | Enter the name (a wildcard is allowed) of the file. When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. |
Application Category Name | Enter the most common types of applications as detected by the Zyxel Device. Application categories include Application Service, Instant Messaging, Web, Encrypted, and so on. When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one application category can be entered after the first filter rule by entering another application category and pressing Enter. Multiple application category filters are entered one at a time. |
Application Name | Enter the most frequently visited applications (a wildcard is allowed) as detected by the Zyxel Application Patrol. App Patrol manages general protocols (for example, HTTP and FTP), instant messenger (IM), peer-to-peer (P2P), Voice over IP (VoIP), streaming (RSTP) applications and even an application’s individual features (like text messaging, voice, video conferencing, and file transfers). When adding this as a filter rule, enter the first letter to enable SecuReporter auto suggestion. More than one application name can be entered after the first filter rule by entering another application name and pressing Enter. Multiple application name filters are entered one at a time. |
Web Category Name | Enter the most common types of threats posed by websites blocked by the Zyxel Device as detected by the URL Threat Filter. Threat categories include Unrated, Anonymizers, Compromised, Phishing and Fraud, Spam Sites, Malware, Botnets, and so on. When adding this as a filter rule, enter the web category name or part of the web category name you want to find to enable SecuReporter auto suggestion. More than one web category name can be entered after the first filter rule by entering another web category name and pressing Enter. Multiple web category name filters can be entered one at a time. |
Website | Enter the name of the website (a wildcard is allowed) tasked with screening for the most common types of threats posed by websites blocked by the Zyxel Devices. When adding this as a filter rule, enter the website or part of the website you want to find to enable SecuReporter auto suggestion. |
Query Type | Enter the type of IP address that may pose a security threat to network devices behind the Zyxel Device. When adding this as a filter rule, select from the drop-down list. More than one query type can be entered after the first filter rule by entering another query type and pressing Enter. Multiple query type filters are entered one at a time. |
Domain | Enter the URL of FQDNs that may pose a security threat to network devices behind the Zyxel Device. When adding this as a filter rule, select from the drop-down list. More than one domain can be entered after the first filter rule by entering another domain and pressing Enter. Multiple domain filters are entered one at a time. |